|
|
TAG: network, infiltrator, security, scanning, information, scanner, , security scanner, network security, network security scanner, security scanner infiltrator, infiltrator network security, Best Search Category: Computers Production, Financial Indicators, Housing Indicators, Interest Rates, Stock Prices, mobile phone contracts, new mobile phone, orange mobile phone, o2 mobile phone, best mobile phone, 3g mobile phone, sharp mobile phone, mobile phone networks, mobile phone tariffs, mobile phone offer
License / Price:
Shareware / 49.95 $
|
Category :
Internet
/ Security
|
Requirements :
2MB Disk Space |
Publisher / Limitations:
Infiltration Systems / 10 Days |
Size / Last Updated:
1.32 MB / 2009-02-05 |
TAG: network, infiltrator, security, scanning, information, scanner, ,
security scanner, network security, network security scanner, security scanner infiltrator, infiltrator network security,
|
Operating System:
Win98, WinME, WinNT 4.x, Windows2000, WinXP, Windows2003, Windows Vista Starter, Windows Vista Home Basic, Windows Vista Home Premium, Windows Vista Business, Windows Vista Enterprise, Windows Vista Ultimate, Windows Vista Home Basic x64, Windows Vista Home Premium x64, Windows Vista Business x64, Windows Vista Enterprise x64, Windows Vista Ultimate x64 |
Download:
Download
|
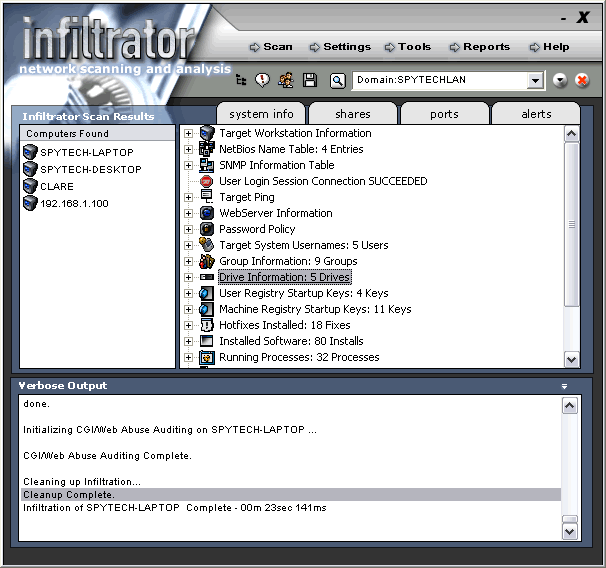
Publisher's description - Infiltrator Network Security Scanner 4.0
Infiltrator is a network security scanner that can quickly audit your network computers for possible vulnerabilities, exploits, and information enumerations. It comes with a built-in database of know vulnerabilities, that can be updated online and allows you to select the items to scan for or to add custom entries to be included. Infiltrator can reveal and catalog a variety of information, including installed software, shares, users, drives, hotfixes, NetBios and SNMP information, open ports and much more. It can also audit password and security policies, perform HTTP/CGI server auditing, registry auditing In addition, Infiltrator also comes with 19 network utilities for footprinting, scanning, enumerating and gaining access to machines (ping sweep, whois lookups, email tracing, share scanning and more). The program can be run from the commandline, allowing for external scheduling and automated scanning.
|
Related app - Infiltrator Network Security Scanner
|
Previous Versions Infiltrator Network Security Scanner 4.0
Infiltrator Network Security Scanner 3.0
Also see ...
...in Internet  1)
PostieX 7.40aE-Mail by Infradig Systems - Software Free Download
1)
PostieX 7.40aE-Mail by Infradig Systems - Software Free Download
A Win32 OCX for internet mail. Supports SMTP, POP3, IMAP4 andNNTP posting....
 2)
Corporate Messenger VCM 2.3.2Chat by Gurpratap Virdi - Software Free Download
2)
Corporate Messenger VCM 2.3.2Chat by Gurpratap Virdi - Software Free Download
The Tools:Encrypted Messaging Chats File transfers Message History Enhanced customization options Easy to understand GUI interface with helps menus Secure core technology with security features 24-Hour support with live online chat support Secure as communication stays on the LAN, never goes onto the internet...
|
...in Security  1)
Adwareflush 9.3.0.10
1)
Adwareflush 9.3.0.10
Adwareflush is a program that protects you from the dangers of the internet, profiteers, and internet criminals. It is available in multi-languages. It scans all user accounts and shreds the detected spyware threats files ....
 2)
BhoScanner
2)
BhoScanner
It is known that the browser helper objects are loaded each time the browser is started up. Such objects run in the same memory context as the browser and can perform any action on the available windows and modules. For ex., a browser helper object can install hooks to monitor messages and actions, etc .Some BHOs are helpful, like the Adobe Acrobat or Google Toolbar Browser Helper Objects, but there could be malicious ones among them that will harm your computer, especially those planted by viru...
|
|
Related tags:
|
|