|
|
More tags: security, monitoring, intelligence, access control, parental control, investigation, surveillance, detective, espionage, spy, key loger, keylogger, trojan, hack, hacking, cheating spouse, internet,
| |
Category : |
Utilities - Security |
|
|
| |
Platform : |
Win95, Win98, WinME, WinNT 4.x, Windows2000, WinXP |
|
| |
Price : |
USD 149.95 |
|
| |
Developer: |
|
|
| |
Rating : |
|
|
| |
License : |
Shareware |
|
| |
Limitations: |
20 Uses |
|
| |
Date : |
02/07/2007 |
|
| |
Size : |
1.16 MB |
|
|
|
Software In :
Utilities
Security
security, monitoring, intelligence, access control, parental control, investigation, surveillance, detective, espionage, spy, key loger, keylogger, trojan, ing, cheating spouse, internet,
|
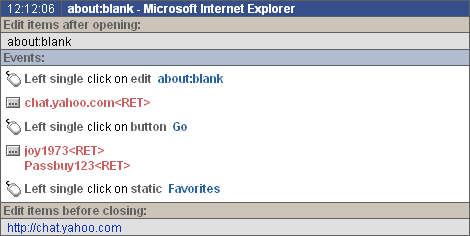
PC Activity Monitor (PC Acme) is an ultimate invisible and undetectable easy-to-use monitoring and surveillance tool for both networked and personal PCs. It is professional software that captures all users activity on the PC. All data collected by the monitoring are saved to encrypted log file. The log file can be optionally sent via e-mail to a specified address (or saved to a specified shared resource in LAN environment) for further inspection and analysis. The important advantage of PC Acme Pro keylogger is an ability to save log files in special database for further analysis and retrieving information by specifying a search condition.It is a powerful management tool for users and companies, which want to increase their productivity and profitability. This is the most remarkable security product for a computer you have seen. Program works in background, transparent for user, and captures the following events: - Application start - Switching between applications/windows. In addition program saves static text elements and windows edit controls: - Window content of most chat clients (ICQ, AIM, Yahoo etc.) - Content of Internet browser window (Internet explorer) - Mail content, viewed by Microsoft Outlook and Microsoft Outlook Express - etc. - Keystrokes - Pasting text from clipboard - File operations - System registry operations - Application installation/uninstallation - Putting programs in Startup folder - Visiting web sites. Log files are converted to HTML format for more convenient viewing in browser (Internet Explorer 4.0 or higher is recommended). Log file can be optionally sent via e-mail to specified address (or saved to specified shared resource in LAN environment) for further inspection and analysis (NET and PRO versions only). The important advantage of PRO version is an ability to save log files in special database for further analysis and retrieving information by specifying a search condition.
WW2 Wargaming SoundboardCoin Toss Pro寰宇新聞A Dog Run Adventure - Best Super Fun Race to Fetch the Bones GameFL Studio Beats GuideMelody D Matthews` Agent Tapp【趣味】映画の感想・掲示板RS-Law |
|
Also See
 1)
Outlook Express Protector
1)
Outlook Express Protector
Outlook Express Protector is designed for controlling access to Outlook Express and its e-mail and address data bases. It does not encrypt protected files and folders, however no programs can get acce...
License:Shareware USD 29
Size:0.62 MB
 2)
InstallBlock
2)
InstallBlock
Install-Block allows you to require a password to be entered in order for new software to be installed on your computer. An ideal solution for parents, employers, and teachers who seek to secure their...
License:Shareware USD 19.95
Size:3.55 MB
 3)
StormWindow 2000
3)
StormWindow 2000
Cetus StormWindow [TM] for Windows 2000 will allow the authorized user to add several types and degrees of protections to the desktop and system of a Windows 2000 computer. Intelligent use of StormWin...
License:Shareware USD 30
Size:1.25 MB
stormwindow, stormwindows, security, cetus, windows, windows 000, windows k, win000, wink, win k, registry, explorer, password,
 4)
IDFile
4)
IDFile
File verification utility, uses SHA-2 algorithm....
License:Freeware USD 0
Size:0.22 MB
 5)
CHAOS Public Key
5)
CHAOS Public Key
CHAOS+PK uses the newest chaos. It is high speed and allows variable-length keys, making protection very reliable and suitable for use in working. Uses the Public Key for encryption CHAOS keys by send...
License:Shareware USD 59.95
Size:0,4 MB
 6)
ANTITHIEFWARE
6)
ANTITHIEFWARE
ANTITHIEFWARE is a program that eliminates all adwares, spywares, viruses, Dialers, and hijackers that might exist on your PC. ANTITHIEFWARE is a program that uses a database with tens of thousands fi...
License:Shareware USD 29.99
Size:0.45 MB
 7)
asquared HiJackFree
7)
asquared HiJackFree
a-squared HiJackFree is a detailed system analysis tool which helps advanced users to detect and remove all types of HiJackers, Spyware, Adware, Trojans and Worms. Manage all types of Autoruns on your...
License:Freeware USD 0
Size:1.54 MB
 8)
Privacy Restorer
8)
Privacy Restorer
Your PC knows a lot about you. What websites you’ve visited. What you’ve seen and downloaded. Your passwords, personal preferences, files you’ve used, programs you’ve installed, your usage hab...
License:Shareware USD 29.95
Size:0.64 MB
 9)
Privacy Keeper
9)
Privacy Keeper
Privacy Keeper is powerful privacy software to erase online Internet tracks and program activity. Privacy Keeper is a safe and easy-to-use privacy protection tool that securely deletes online Internet...
License:Freeware USD 0
Size:6.8 MB
 10)
Beautiful Spyware Remover
10)
Beautiful Spyware Remover
Beautiful Spyware Remover is a popular and easy-to-use tool, Is the only company in the world that offers a 100% removal guarantee. Why accept a "solution" with anything less than 100%? With Beautiful...
License:Shareware USD 59.95
Size:2.12 MB
Tags: spyware, adware, remove, antispyware, remover, removal, spyware remover, remove spyware, adware remover
|
 1)
Max Secure Content Audit Enterprise
1)
Max Secure Content Audit Enterprise
Content Audit is a revolutionary new software tool designed to detect the presence of inappropriate content, files and programs, which are Enterprise non-complainant. An extensive search can be perfor...
License:Shareware USD 29.95
Size:3.18 MB
 2)
123 Spyware Free Mobile
2)
123 Spyware Free Mobile
Keep your PC protected from Internet threats with a free USB Flash Drive-based anti-spyware and antivirus solution that is always with you. Keep your antivirus flash card always with you for ultimate ...
License:Freeware USD 0
Size:6.70 MB
 3)
Backup Manager
3)
Backup Manager
Backup Manager offers a 2 Week Free Trial - with no further obligation - of its automated, encrypted (128 bit encryption technology), offsite data backup service. Download the software and upload your...
License:Commercial USD 3.95
Size:2.10 MB
online backup, remote backup, internet backup, data backup, offsite backup, web backup,
 4)
OnTap PLUS SCO
4)
OnTap PLUS SCO
On-Tap Plus lets you print bar codes from any application on any printer.Simply surround the information to bar code with a special character and you can print UPC, EAN, Code 39, I2 of 5, MSI, PostNet...
License:Demo USD 695
Size:0.79 MB
 5)
Pocket File Manager
5)
Pocket File Manager
Do you want more efficiency from a Windows Mobile file explorer? Pocket File Manager is the solution. It is an advanced, yet easy to use, Windows Mobile file manager based on the dual window pane conc...
License:Shareware USD 19.95
Size:0.27 MB
 6)
Advanced Office Password Recovery
6)
Advanced Office Password Recovery
Advanced Office Password Recovery is a program to recover lost or forgotten passwords to files/documents created in Microsoft Office components (all versions up to Office 2003) and other Microsoft sof...
License:Shareware USD 199
Size:2.71 MB
 7)
HSLAB Sys Monitor Pro
7)
HSLAB Sys Monitor Pro
Advanced real-time monitoring and statistics utility for Windows. HSLAB Sys Monitor uses some advanced technologies for logging and mesuring system components. The sensors permanently monitor behind p...
License:Shareware USD 24.92
Size:2.03 MB
 8)
Audio Zone Trigger
8)
Audio Zone Trigger
Audio Zone Trigger is a sound detection software. It takes live audio from any input source and enables the computer to react to it in a user-specified manner. The sound-detection system lets you set ...
License:Shareware USD 24.95
Size:1.94 MB
 9)
Password Recovery .MDB
9)
Password Recovery .MDB
Have you lost the Password of your database Access? Don't worry more, you can already recover it with this great program. Password Recovery. MDB is a program dedicated to that you can recover lost or ...
License:Shareware USD 12
Size:1.95 MB
 10)
EMail Image Generator
10)
EMail Image Generator
Spam messages can be called the scourge of all Internet users nowadays. According to recent studies, half of email messages received by active users are spam messages, which results in a number of und...
License:Shareware USD 19.95
Size:1.19 MB
Tags: email, image, tool, protection, spam, filter, spam filter
|
|
More tags: security, monitoring, intelligence, access control, parental control, investigation, surveillance, detective, espionage, spy, key loger, keylogger, trojan, ing, cheating spouse, internet,
|
|