|
|
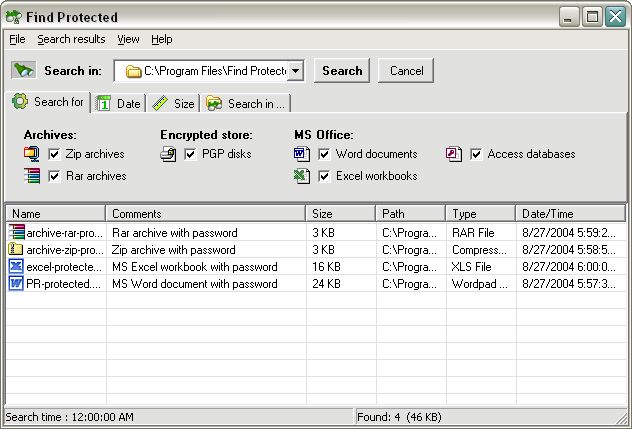 | T2U is a software deployment, patch management and license tracking system. T2U dramatically decreases number of software products included into the main packages. Since designing large packages is costly it always saves a good deal of money. With T2U everybody in your company may devote more time t...
|
CERTIFOOT FRANCE - Snapdragon™ BatteryGuru (Beta) - Map And Directions - Nama Bayi Islami Lengkap - Barney & Friends Wallpapers -
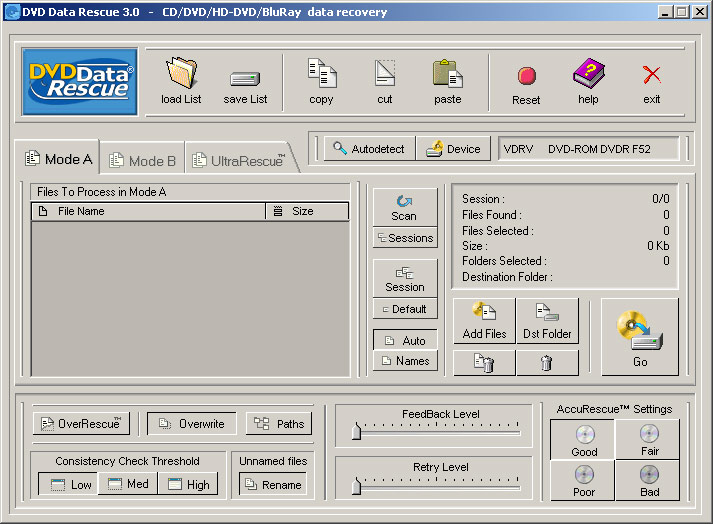 | DVD Data Rescue is a windows based application designed specifically to recover lost and deleted files from damaged, scratched or defective CD/DVD/HD-DVD/BluRay discs. With this products you can easily recover unreadable files, folders, or deleted files. Includes the UltraRescue recovery mode for co...
|
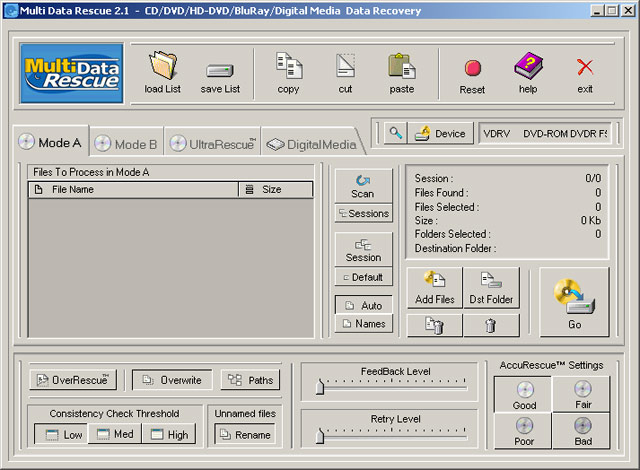 | Multi Data Rescue is a windows based application designed specifically to recover lost and deleted files from damaged, scratched or defective CD/DVD/HD-DVD/BluRay discs and Digital Media. With this product you can easily recover files, folders, or deleted files from discs and Digital Media. Includes...
|
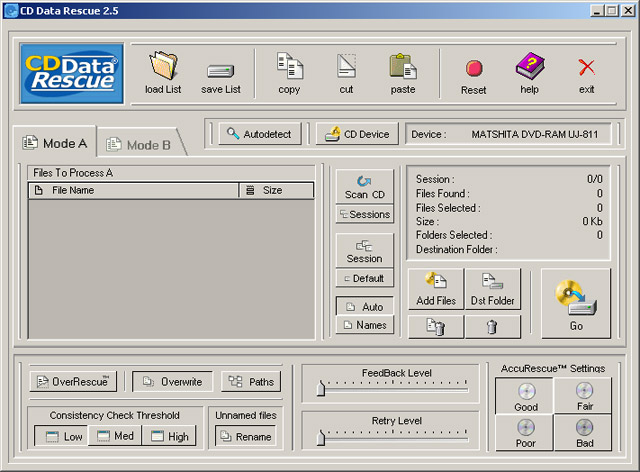 | CD Data Rescue is a effective data recovery software that recovers lost,unreadable and deleted files from damaged,scratched or defective CD-ROM, CD-R and CD-RW discs,supporting also Mount Rainier/MRW discs even in not compilant drives. With this products you can easily recover files, folders, or del...
|
 | Java Keystroke and Mouse Event Tutor / Keyboard Diagnostic Application to let you experiment to learn how mouse and keystroke events work. Output appears on the console. Just click the mouse or hit keystrokes and watch what details of the events generated. To install, Extract the zip download with W...
|
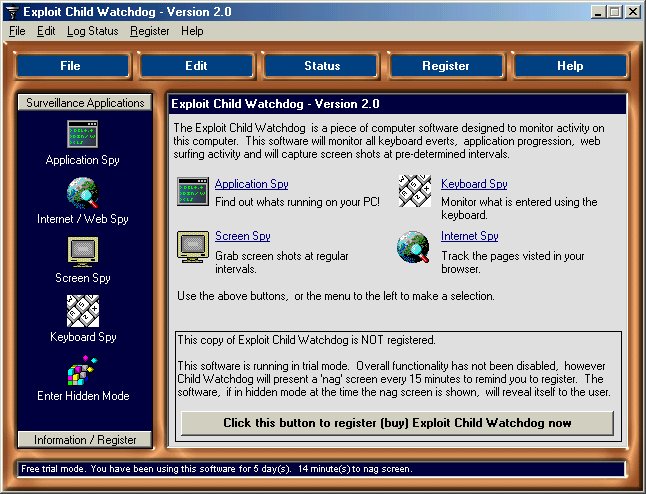 | The Child Watchdog software has been designed to help parents of older kids (11+) obtain peace of mind. The software gives you, the parent, a method of checking what your children have been using your computer for, in your absence, without them knowing. With the Exploit Child Watchdog, you now have ...
|
Defpix (in System Utilities)
 | Defpix - Defective (dead) pixels tester is a free program that can help you with checking for defective pixels on your LCD screen. The program simply shows these colors - red, green, blue, white and black - over the whole surface of the screen. Defpix requires no installation and supports multiple m...
|
 | RemoteShutdown allows an NT/2K/XP Administrator to remotely shutdown any number of NT/2K/XP Workstations over which they have administrative control via either a GUI interface or a command-line interface. You can specify a delay, which can either be an absolute time (eg. 8pm) or a relative time (eg....
Tags: coruscant, remote, shutdown, nt, delayed, reboot, restart, network, users, log off, log out, server, power-off, apm, windows, admin, administrator, domain, pdc, cluster, trust relationship, |
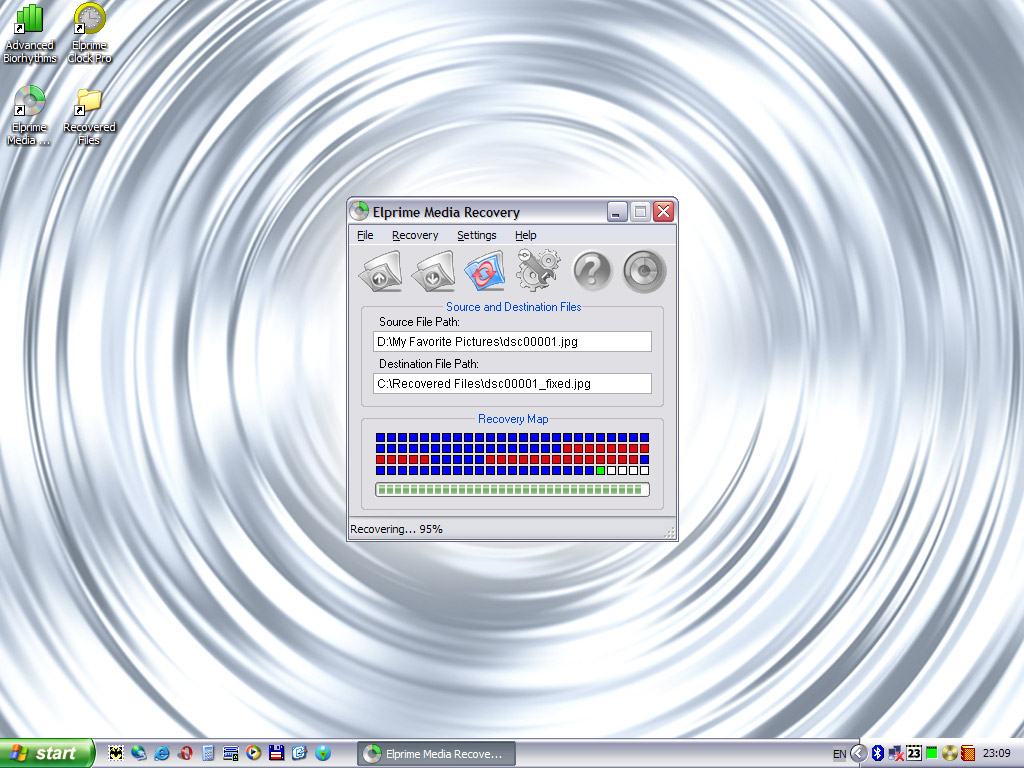 | Recover files from heavily scratched, damaged or defective CD and DVD disks, USB flash drives, memory cards, floppy disks and other storage media. Elprime Media Recovery uses an advanced data recovery technology to access and recover unreadable files in Windows operating system. Elprime Media Recove...
|
 | BadCopy Pro is a leading data recovery tool for floppy disk, CD-ROM, CD-R/W and other storage media. It can effectively recover and rescue corrupted or lost data from damaged, unreadable or defective disks. Various damage situations and all file types are supported....
|
 | Features: - Creates a virtual encrypted disk within a file and mounts it as a real disk - Encryption is automatic, real-time (on-the-fly) and transparent - Parallelization and pipelining allow data to be read and written as fast as if the drive was not encrypted - Provides plausible deniability, in ...
Tags: smart card, disk, encryption csp, pkcs, hba, egk, sagemorga, qs, belpic, infocamere, telesec, d-trust, multicard, pm, ps, pkcs, |
|
|











