Publisher's description - Network Spy
Network Spy is a general purpose diagnostic tool for administrators,
programmers and students of network technologies. It can operate in
different modes depending on the application. Some of the more typical
applications of this tool include: <Br>
<blockquote>
<ol>
<li>Packet capture and decode
<li>Network Statistics gathering
<li>Software debugging
<li>Intrusion Detection and activity monitoring
</ol>
</blockquote>
<b><u>Packet Capture and Decode</u></b><br><br>
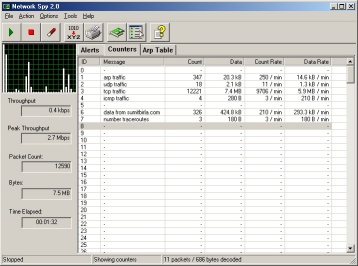
In this mode, Network Spy can be used to get a snapshot of data from an
ethernet network. It is capable of decoding the most widely used IP
protocols such as UCP, TCP and ICMP. It also allows you to save this data
for later analysis. The decoded packets are displayed in human readable
form.<br><Br>
<b><u>Network Statistics gathering</u></b><br><br>
In this mode, the amount of data attributed to a certain activity can be
captured. For instance, if you want to monitor how much data is
transferred between user x and excite.com, you can specify a rule to keep
a track of amount of this data. Another example is keeping track of how
much FTP data flows on your network.<br><br>
<b><u>Software Debugging</u></b><br><br>
People programming network software and web applications will find this
tool extremely useful. It can be used to debug application to find errors
in code, compute bandwidth utilization and find bottlenecks. <br><br>
<b><u>Intrusion Detection and Activity Monitoring</u></b><br><br>
Using the new rules-based filtering mechanism, one can capture packets of
interest, avoiding a huge capture of all packets on the network. A rule
specifies a pattern to match. For instance, one could specify to capture
all ICMP packets where TTL=1. This would be true when someone is
performing a traceroute.
Network Spy also includes various other tools such as DNS Lookup, Ping, TraceRoute and Whois to aid in everyday tasks.