|
|
More tags: security, monitoring, intelligence, access control, parental control, investigation, surveillance, detective, espionage, spy, key loger, keylogger, trojan, hack, hacking, cheating spouse, internet,
|
|
|
|
PC Activity Monitor Net (PC Acme Net)
|
|
| |
Category : |
Utilities - Security |
|
|
| |
Platform : |
Win95, Win98, WinME, WinNT 4.x, Windows2000, WinXP |
|
| |
Price : |
USD 89.95 |
|
| |
Developer: |
|
|
| |
Rating : |
|
|
| |
License : |
Shareware |
|
| |
Limitations: |
20 Uses |
|
| |
Date : |
02/19/2007 |
|
| |
Size : |
0.96 MB |
|
|
|
Software In :
Utilities
Security
security, monitoring, intelligence, access control, parental control, investigation, surveillance, detective, espionage, spy, key loger, keylogger, trojan, ing, cheating spouse, internet,
|
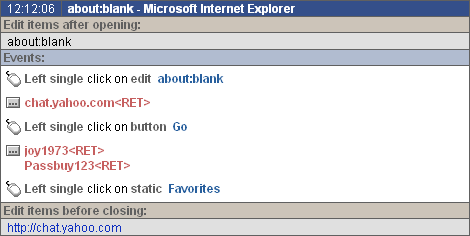
PC Activity Monitor Net™ is ultimately invisible and undetectable easy-to-use surveillance software for both networked and personal PCs. It is professional keylogger software that captures all users' activity on the PC. All data collected through the monitoring are saved to an encrypted log file. The log file can be optionally sent via e-mail to a specified address (or saved to a specified shared resource in LAN environment) for further inspection and analysis. It is a powerful management tool for users and companies, which want to increase their productivity and profitability. This is the most remarkable security product for a computer you have seen. Program works in background, transparent for user, and captures the following events: - Application start - Switching between applications/windows. In addition program saves static text elements and windows edit controls: - Window content of most chat clients (ICQ, AIM, Yahoo etc.) - Content of Internet browser window (Internet explorer) - Mail content, viewed by Microsoft Outlook and Microsoft Outlook Express - etc. - Keystrokes - Pasting text from clipboard - File operations - System registry operations - Application installation/uninstallation - Putting programs in Startup folder - Visiting web sites. Log files are converted to HTML format for more convenient viewing in browser (Internet Explorer 4.0 or higher is recommended). Log file can be optionally sent via e-mail to specified address (or saved to specified shared resource in LAN environment) for further inspection and analysis (NET and PRO versions only).
MultiCamPlus TorontoTendenceBarber for Gansters PROQuick Scanner - Scan Documents & Convert to PDF & Image to TextCE on the go MobileZombie Boot Campزخارف اسلامية متنوعة |
|
Also See
 1)
Folder Guard Professional
1)
Folder Guard Professional
Snoop-proof your files with Folder Guard. Folder Guard is a Windows security program which you can use to restrict access to files, folders, and other computer resources. If you share your computer wi...
License:Shareware USD 59.95
Size:2.45 MB
 2)
My Safety Pin
2)
My Safety Pin
Aid to remembering your pin numbers. Stores your pin number within a table of random numbers which you print out. Easily retrieve your number using word keys. A Pin Wizard guides you step by step conv...
License:Shareware USD 12.00
Size:0.52 MB
 3)
IPTunnelManager
3)
IPTunnelManager
The program IPTunnelManager is used for IP tunneling with the options for compressing and encrypting traffic. Thus, the program makes it possible to create a secure connection for any application or s...
License:Shareware USD 49
Size:1.59 MB
internet intranet telnet proxy secure compress encrypt traffic dbms database client server network communication ftp ssl ssh blowfish zlib winsock ipsec mac hash security tunnel tunneling port forwarding,
 4)
Advanced Drive Protector
4)
Advanced Drive Protector
Password-protect, hide and lock your local, network, Floppy, CD/DVD and USB drives with Advanced Drive Protector. Disable the AutoRun feature for the selected drives to prevent unauthorized software i...
License:Shareware USD 39
Size:0.53 MB
 5)
Free Privacy Fix
5)
Free Privacy Fix
Free Privacy Fix will securely and permanently delete any traces of your online and offline activity so that you can enjoy the freedom you enjoy in other aspects of your life. No-one watches you when ...
License:Freeware USD 29.95
Size:3.88 MB
 6)
PC Locker Pro
6)
PC Locker Pro
PC Locker Pro V1.2 Copyright(c) Silver Eagle Software,Inc. All Rights Reserved. http://www.SilverEagleSoft.com http://www.cute-cd-dvd-burner.com Email: contact@silvereaglesoft.com Introduction PC Lock...
License:Freeware
Size:0.57 MB
 7)
FreeShield
7)
FreeShield
As well as powerful, extensive customisable parental controls Freeshield also include many other features. FreeShield also provides antivirus/anti-adware protection, a popup blocker and a facility to ...
License:Freeware
Size:0.65 MB
 8)
Internet Secure Tunneling
8)
Internet Secure Tunneling
Internet Secure Tunneling can forward otherwise insecure TCP traffic through encrypted SSH Secure Shell tunnel. You can secure for example DATABASE, POP3, SMTP and HTTP connections that would otherwis...
License:Shareware USD 35.99
Size:0.90 MB
 9)
Password strength analyzer and generator
9)
Password strength analyzer and generator
The Password Strength Analyser and Generator is one application combining three tools - the Analyser (shows the "strength" of your pass phrase regarding some rules), the Generator (generates "strong" ...
License:Freeware USD 0
Size:0.12 MB
 10)
Love You Not
10)
Love You Not
Love You Not! will intercept any request to execute all scripting file types used in email virus attacks. These include: Visual Basic scripts (.VBS, .VBE, .VB), Javascript (.JS, .JSE), Scrap objects (...
License:Shareware USD 5.00
Size:0.87 MB
Tags: email, outlook, protection, script, scripts
|
 1)
Matrix V Encryption
1)
Matrix V Encryption
Free Unbreakable encryption software - Matrix V. "Make your secrets unbreakable!" Nobody, absolutely nobody, not even the NSA, can decrypt communications using Black Matrix. Because most computer user...
License:Freeware USD 0
Size:0.44 MB
 2)
Easy Desktop Keeper
2)
Easy Desktop Keeper
Easy Desktop Keeper gives you the ability to save, restore, manage and lock your desktop layout including files and folders located on your desktop, placement of desktop icons, desired wallpaper and s...
License:Shareware USD 49
Size:0.71 MB
 3)
ID Parental Advisor
3)
ID Parental Advisor
ID Parental Advisor is a utility program designed to block porn sites from opening in your Internet Browser. Using an integrated database focused on certain keywords, it scans and finds adult-content ...
License:Shareware USD 47
Size:0.79 MB
children, kid, nanny, block, conten, parent, parental, parental advisor, id parental advisor, protect, privacy, internet, clean, erase, shield, spyware, antispyware, security suite,
 4)
Heidi R. Stealthy (TM)
4)
Heidi R. Stealthy (TM)
With a single mouse-click, Heidi R. Stealthy (TM) allows you to instantly conceal your current PC or laptop activities from your friends, family, coworkers, roommates, casual onlookers and passersby. ...
License:Shareware USD 8.95
Size:0.56 MB
 5)
Keylogger King Pro
5)
Keylogger King Pro
I want to share with you my experience of using Keylogger King Pro. In our department, we use several methods of work-time effectiveness control. One of them, a daily report, was our best achievement ...
License:Shareware USD 39.95
Size:1.39 MB
 6)
Eusing Free Registry Cleaner
6)
Eusing Free Registry Cleaner
Eusing Free Registry Cleaner is a free registry repair software that allows you to safely clean and repair registry problems with a few simple mouse clicks.The Windows Registry is a crucial part of yo...
License:Freeware USD 0
Size:0.89 MB
 7)
Advanced VBA Password Recovery
7)
Advanced VBA Password Recovery
A program to recover or remove lost or forgotten passwords to view and edit Visual Basic for Applications (VBA) projects source code in Microsoft Office documents: Word and Excel (97, 2000, XP, 2003),...
License:Shareware USD 49
Size:0.7 MB
 8)
EF CheckSum Manager
8)
EF CheckSum Manager
EF CheckSum Manager is a program designed for the integrity examination of files on the standard formats SFV, MD5 and SHA1. They can verify existing checksums or create new checksum for your important...
License:Shareware USD 14
Size:1.46 MB
 9)
Keylogger Stopper
9)
Keylogger Stopper
Keylogger Stopper is a sophisticated software to disable keylogger from working on your PC. Using highly efficient technology, Keylogger Stopper will monitor all keylogging activities and disable them...
License:Shareware USD 16
Size:0.65 MB
 10)
WinPSF
10)
WinPSF
WinPSF is designed to archivization and data backup with established profiles. Automatically compress and stores selected data. Can do it on user's command (HotKey keys, profiles to select from tray i...
License:Shareware USD 32
Size:1.33 MB
Tags: data, archive, compress, pack
|
|
More tags: security, monitoring, intelligence, access control, parental control, investigation, surveillance, detective, espionage, spy, key loger, keylogger, trojan, ing, cheating spouse, internet,
|
|