|
|
Order by Related
- New Release
- Rate
Results in Title For bytes out
 | Watch your clock - this game is fascinating! Bubblet is an easy but fascinating Logic-Game. Match as much Bubbles in one color in order to burst them! The more are alligned together, the more points you .. |
|
 | A new protection for programms. Implementing TrialL0CK in programs is very easy and it works with every programming language capable of loading libraries ..
|
|
Results in Keywords For bytes out
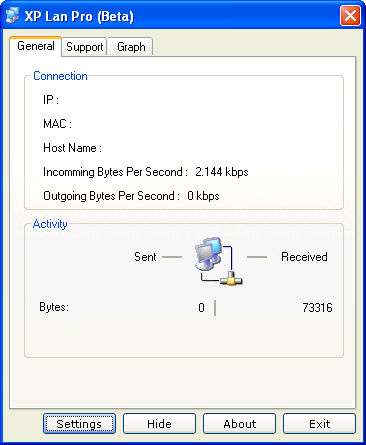 | Feathers :
These are overall features of XP Lan Pro 3.3 (Beta).
XP Lan Pro 3.3 (Beta) can determine following things.
IP address of your computer,
MAC address of LAN card,
Host Name Determination,
Subnet Mask of your network,
DNS Server,
DHCP Server,
Incomming Bytes Per Second,
Outgoing Bytes Per Second,
Incomming Bytes per second Graph,
Outgoing Bytes per second Graph.
In this version XP Lan Pro you can Use System Tray Icon or Bar.You can Change Tray Icon
Lights Colours.When you move you mouse to the tray icon of XP Lan Pro it shows you Total
bytes sent and Total bytes recive... |
|
 | Easy File Splitter is a piece of beautiful software for splitting large file to smaller files by bytes, kilo bytes, mega bytes, lines. Join splitted files to the original file. Use Easy File Splitter to split files into pieces so that you can move them between systems on floppy disks, or email them out sharing with your friends over the Internet...
|
|
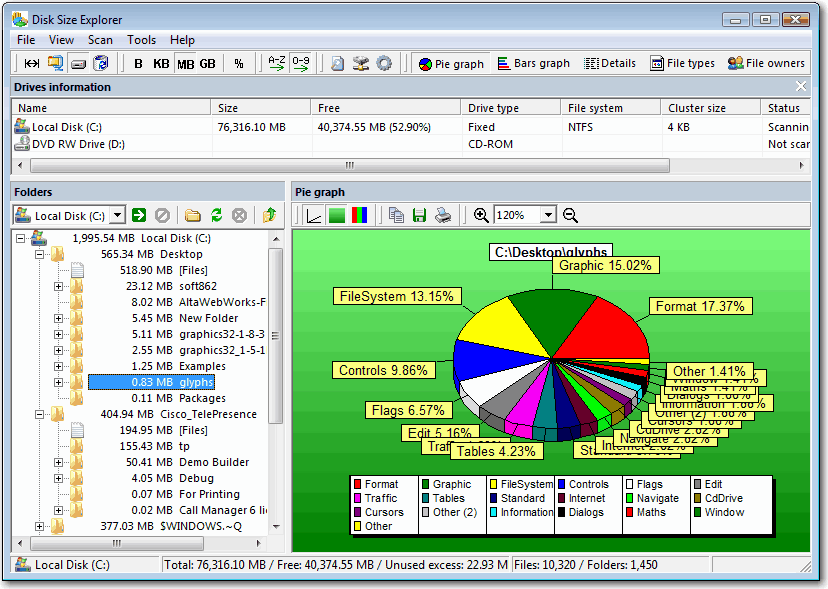 | Disk Size Explorer - Special Offer - Disk space directory folder size usage analysis management software.. |
|
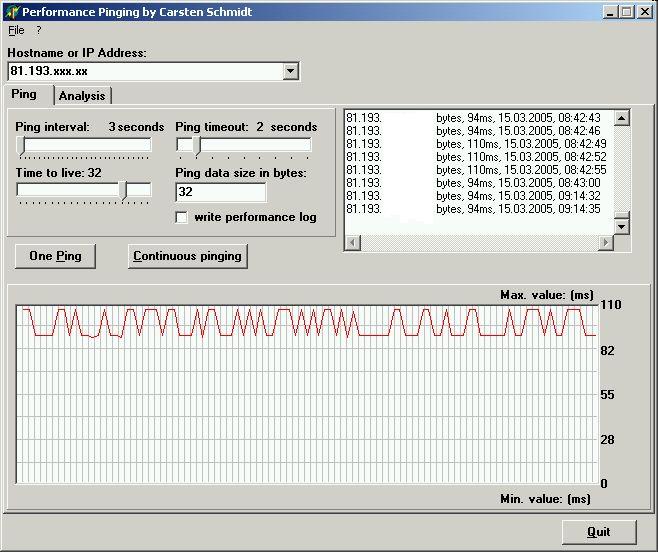 | Performance Pinging, Perfping.exe
Version 2.0.0; March 2006
How does it work and what does it do?
Perfping is a tool that allows you to ping a host continuously or with a single
ping using different data volumes. This can give you an indication of the
performance of the route to your host. You can change the ping interval from 2
to 30 seconds using various timeouts. The timeout is always smaller than the pinging
interval. Results are written to log window and log file if so chosen.
Unreachable hosts have a value of 0 ms.
The analysis function sends various pings, 10 each of 10 bytes, 100 bytes, 500
bytes, 1 kbytes, 10 kbytes, 50 kybytes and 64 kbytes. The round trip times are
shown with the total and average times.
Comments:
- Errors are written to file and log window but may be shown later than
successfull pings when changing ping intervall and timeout during runtime
- Thanks to Francois Piette for the internet component suite, Angus Robertson
for the threaded version of Ping and Dr. Jurgen Kehrel for the graph component...
|
|
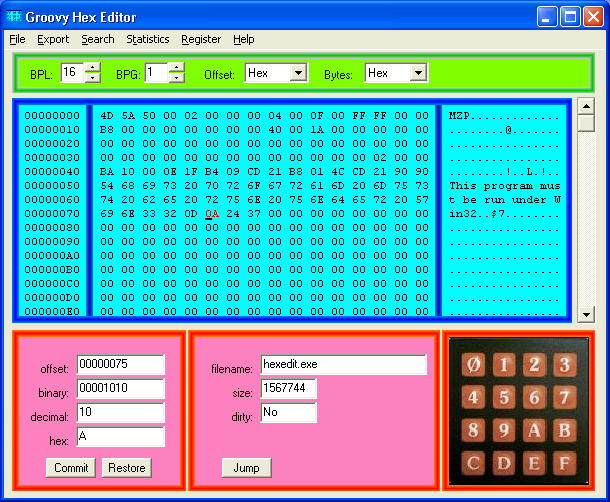 | Groovy Hex Editor is a tool for editing binary formats. I've paid particular attention to making it colorful and easy to use and tried to give it a cool looking color scheme (hence the name "groovy" hex editor). You can also downgrade it to a "standard" windows color scheme if thats more to your liking. It's a fully functional hex editor with many advanced features. You can toggle the display between hex and decimal, and there is a built in inspector that easily lets you see the hex, decimal, and binary equivalents of a group of bytes at once. You can easily control the number of bytes displayed per line, and the number of bytes per group. This makes it excellent for viewing various data types (bytes, words, long words, etc). The program features multi-level undo and redo features that let you quickly fix mistakes. There's even a changelog that lets you keep track of what modifications you've made to the current file. The main window is color-coded (and configurable) so that you can highlight different items in different colors. Various tools are built in, including a string sifter feature that automatically pulls all of the ascii strings out of the file, so that you can see all the strings in one convenient place. This program features the SB-Software no-hassle guarantee: no spyware, no adware, no viruses, no expiration, and no disabled features... |
|
 | TEXTCODE, this is an application that takes a binary file and converts it to printable text.This application is similar to endecrypt but it has an output of Printable text. This would allow any type of file, i.e. software, image or text file to be sent as a paper printout by s-mail or messenger. The cipher must be sent separately. It uses an encryption method that is difficult to crack without sophisticated decryption applications. A password generating program will need to have the exact password before any sense can be made of the code.The Textcode application can generate one of two types of file BINHEX (1 binary byte to 2 Text bytes), or an output file that inputs 3 binary bytes and outputs 4 text bytes. In the BINHEX option there is optional encryption using the same engine as endecrypt. It will also take the output file and reconvert it to a binary file. ..
|
|
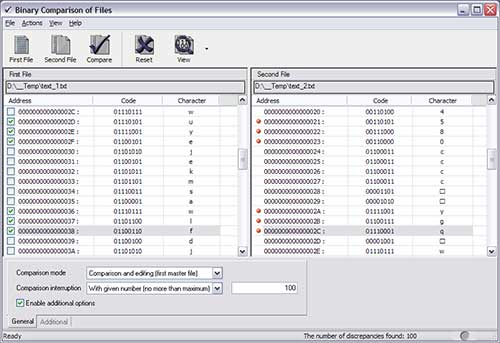 | Binary Comparison of Files is the utility for comparison of two files in order to find possible distinctions. Consistently read - out bytes of files are compared in a binary mode. The address, code and symbolical representation are shown for different bytes. The codes may be shown as decimal, hexadecimal or octal numbers. The found distinctions may be saved as a text file, exported to Excel or printed.
Main Features
1. Byte-to-byte comparison of files of any format.
2. Viewing of the found distinctions in any code.
3. Saving of the results as a file or a printed document.
4. Convenient and adjustable viewing of the comparison results.
5.Easy-to-use interface.
What's New in 2.0 Version
1. Opportunity to compare files of different length.
2. Saving of the comparison results as a text file.
3. Export of the comparison results to Excel.
4. Printing of the comparison results.
5. Optimization of algorithms of comparison and list view updating with the change of code of different bytes... |
|
 | ExeIcon.com Exe password lock exe file to protect it from non-authorized execution or copy. Add a little more size (about 2k bytes); Custom the password-box notice; Keep the original file icon unchanged.Identify the computer intellectually; Show the password in special time. Can not get original exe file without password; Operate easily; Absolutely safe; Launch with high speed, all operations are in memory; Encrypt all size exe file, from k bytes to M bytes. Exe-file encrypted will show password dialog box before launching exe-file. You are allowed to set the password caption and wrong password notice. The encrypted exe-file can distinguish your computer from others. So if you set ' Needn't password on my computer', then there will be no password needed on your computer. But when the file is copied to other computers the password-box will pop-up every time before running. This will forbid the exe-file being copied to other computers without your authorization. It also allows you to give someone a limited evaluation. For example, if you want others to launch your exe-file before 01/01/2005, the password box will not be shown before this date. But after that, the password will popup when others try to launch it. It protects your exe-file with high strength encryption. But the exe will keep it's original characters such as structure, icons, resources, sections and so on, with only a small size increased ( about 2k bytes ). You can copy your encrypted exe-file to any computer. And needn't worry about the file being copied. But do not forget your password. We can not help you if you lost your password. Certainly, if you provide the password, the exe-file can be decrypted easily. The decrypted exe-file will be the same as the original one... |
|
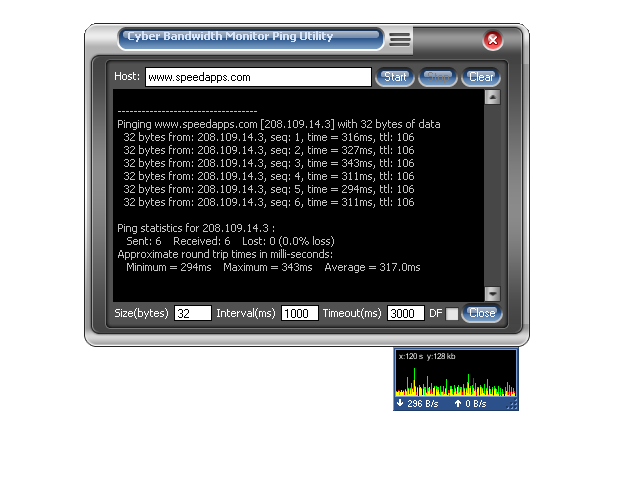 | Cyber bandwidth monitor helps keeping a close eye on the comings and goings of your bits and bytes. A graphing tool that shows your PC's upload and download activities in real time. Additionally Cyber Bandwidth Monitor bundles in some useful networking tools, like ping, traceroute, and IMAP and POP email notifiers. The graphs are highly configurable, show upload and/or download traffic, and can monitor any and all network interfaces.
Key Features:
- Graph of bandwidth usage, show download only, upload only, or both.
- Iconified Graph of bandwidth usage in Systray allows hiding of main graph when it is an obstruction.
- Display units in bits or bytes or both.
- Configurable connection speed (graph scale) and update interval.
- Monitor any or all network interfaces installed in your computer.
- Select colors and transparency of the graph.
- Log total bytes, time, and averages to an html or text file.
- View graph of last 24 hours stats.
- URL grabber watches clipboard for URLs, removes line breaks and opens them in your browser.
- Email notifier can check up to 5 POP/IMAP email accounts for new messages periodically.
- Graphic Ping and Traceroute utilities to help diagnose network problems.
- UPnP NAT utility for those who have compatible Internet Gateway Device detected in Windows Networking... |
|
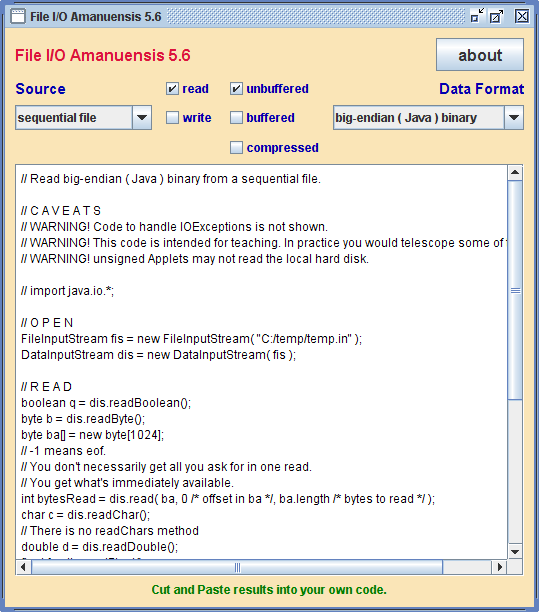 | I/O teaching tool that generates sample Java source code to do 378 types of I/O to read or write the console, a sequential file, a random access file, a String, an array of characters, an array of bytes, URL, HTTP CGI GET/POST, Socket or Pipe... |
|
Results in Description For bytes out
 | TEXTCODE, this is an application that takes a binary file and converts it to printable text.This application is similar to endecrypt but it has an output of Printable text. This would allow any type of file, i.e. software, image or text file to be sent as a paper printout by s-mail or messenger. The cipher must be sent separately. It uses an encryption method that is difficult to crack without sophisticated decryption applications. A password generating program will need to have the exact password before any sense can be made of the code.The Textcode application can generate one of two types of file BINHEX (1 binary byte to 2 Text bytes), or an output file that inputs 3 binary bytes and outputs 4 text bytes. In the BINHEX option there is optional encryption using the same engine as endecrypt. It will also take the output file and reconvert it to a binary file. .. |
|
 | Groovy Hex Editor is a tool for editing binary formats. I've paid particular attention to making it colorful and easy to use and tried to give it a cool looking color scheme (hence the name "groovy" hex editor). You can also downgrade it to a "standard" windows color scheme if thats more to your liking. It's a fully functional hex editor with many advanced features. You can toggle the display between hex and decimal, and there is a built in inspector that easily lets you see the hex, decimal, and binary equivalents of a group of bytes at once. You can easily control the number of bytes displayed per line, and the number of bytes per group. This makes it excellent for viewing various data types (bytes, words, long words, etc). The program features multi-level undo and redo features that let you quickly fix mistakes. There's even a changelog that lets you keep track of what modifications you've made to the current file. The main window is color-coded (and configurable) so that you can highlight different items in different colors. Various tools are built in, including a string sifter feature that automatically pulls all of the ascii strings out of the file, so that you can see all the strings in one convenient place. This program features the SB-Software no-hassle guarantee: no spyware, no adware, no viruses, no expiration, and no disabled features...
|
|
 | Binary Comparison of Files is the utility for comparison of two files in order to find possible distinctions. Consistently read - out bytes of files are compared in a binary mode. The address, code and symbolical representation are shown for different bytes. The codes may be shown as decimal, hexadecimal or octal numbers. The found distinctions may be saved as a text file, exported to Excel or printed.
Main Features
1. Byte-to-byte comparison of files of any format.
2. Viewing of the found distinctions in any code.
3. Saving of the results as a file or a printed document.
4. Convenient and adjustable viewing of the comparison results.
5.Easy-to-use interface.
What's New in 2.0 Version
1. Opportunity to compare files of different length.
2. Saving of the comparison results as a text file.
3. Export of the comparison results to Excel.
4. Printing of the comparison results.
5. Optimization of algorithms of comparison and list view updating with the change of code of different bytes... |
|
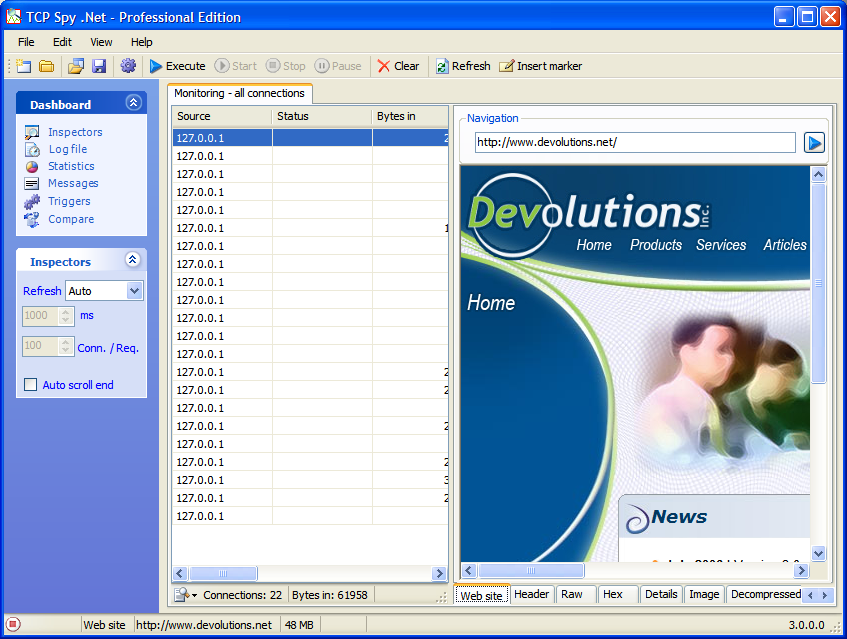 | TCP Spy .NET is a small application used to trace TCP packets between a client and a server. Optimized for .NET Web Services or Web Site TCP Spy .NET will help you find any bottleneck and it will help you in analyzing your bandwidth usage. With TCP Spy .NET, you can inspect data in different views, track server calls or just redirect the host.
It's a 4 in 1 tool:
- monitoring tool
- web service / web site profiling tool
- redirection server
- Network / Web Site / Web Services spy
Features:
1. General
- Light (one file only)
- Small (less than 1 meg)
- Rich and easy user interface
- Auto update
- Free
2. Monitoring
- Monitor connection IP address
- Monitor connection destination
- Monitor opened connection
- Log connections and requests to file
- Suspend monitoring with no service interruption
- Flag connection / request for an easier tracking
- Insert grid marker for an easier tracking
- View and clear log file
3. Profiling
- Profile Web Service: calls, durations, bytes in, bytes out
- Profile Url: content, size
- Get stats about Web Service (calls, duration, bytes in, bytes out)
- Get stats about Url (calls, duration, bytes in, bytes out)
- Pause profiling without interrupting the communication
- Get the size and the duration of the each request
- View request details for each connections
4. Redirection server
- Configure port redirection
- Configure ip redirection
5. Network spy
- Inspect bytes in data
- Inspect bytes out data
- Inspect header and raw data
- View HTTP header
6. Profesional features
- Hex Data view
- Decompressed Data view with supoprt of gzip and deflate
- Xml Data view
- Image Data View
- Summary view
- Statistic view with chart grouped by Web Service, by content or by url
- Trigger notification unexpected data size or duration
- Run in the tray icon
- Tray icon balloon trigger notification
- Save and load p..
|
|
 | ExeIcon.com Exe password lock exe file to protect it from non-authorized execution or copy. Add a little more size (about 2k bytes); Custom the password-box notice; Keep the original file icon unchanged.Identify the computer intellectually; Show the password in special time. Can not get original exe file without password; Operate easily; Absolutely safe; Launch with high speed, all operations are in memory; Encrypt all size exe file, from k bytes to M bytes. Exe-file encrypted will show password dialog box before launching exe-file. You are allowed to set the password caption and wrong password notice. The encrypted exe-file can distinguish your computer from others. So if you set ' Needn't password on my computer', then there will be no password needed on your computer. But when the file is copied to other computers the password-box will pop-up every time before running. This will forbid the exe-file being copied to other computers without your authorization. It also allows you to give someone a limited evaluation. For example, if you want others to launch your exe-file before 01/01/2005, the password box will not be shown before this date. But after that, the password will popup when others try to launch it. It protects your exe-file with high strength encryption. But the exe will keep it's original characters such as structure, icons, resources, sections and so on, with only a small size increased ( about 2k bytes ). You can copy your encrypted exe-file to any computer. And needn't worry about the file being copied. But do not forget your password. We can not help you if you lost your password. Certainly, if you provide the password, the exe-file can be decrypted easily. The decrypted exe-file will be the same as the original one... |
|
 | Q: I have 3D GameStudio; what is the CR Pack Light for 3D GameStudio?
A: Smaller size of published game. For example, Demo #3 in this package has 7 620 886 bytes uncompressed and 4 200 152 bytes compressed. We have ~55% compression ratio, not so bad.
A: Protection of your work. Password encoding, data compression and encryption used. CR Pack Light doesn't decompress resources to a hard drive, but into engine's buffers in memory directly. If you use this package, there is no simple solution to steal your work. It is possible, but harder.
A: Good tool CRED (Custom Resources Editor) to manage your resource packages...
|
|
 | Performance Pinging, Perfping.exe
Version 2.0.0; March 2006
How does it work and what does it do?
Perfping is a tool that allows you to ping a host continuously or with a single
ping using different data volumes. This can give you an indication of the
performance of the route to your host. You can change the ping interval from 2
to 30 seconds using various timeouts. The timeout is always smaller than the pinging
interval. Results are written to log window and log file if so chosen.
Unreachable hosts have a value of 0 ms.
The analysis function sends various pings, 10 each of 10 bytes, 100 bytes, 500
bytes, 1 kbytes, 10 kbytes, 50 kybytes and 64 kbytes. The round trip times are
shown with the total and average times.
Comments:
- Errors are written to file and log window but may be shown later than
successfull pings when changing ping intervall and timeout during runtime
- Thanks to Francois Piette for the internet component suite, Angus Robertson
for the threaded version of Ping and Dr. Jurgen Kehrel for the graph component... |
|
 | Data Copier 2004 is most powerfull software for copying unreadble files from bad media for Windows (TM).
Here are some key features of Data Copier 2004:
Powerfull file copying from all popular media (CD, Diskette, DVD...).
Very fast byte copy process with 16 different speed buffers from 8 bytes to 4 mb.
Support changing unreadble byte-s with new byte which you can choose manually or from another file.
Reading and writing byte buffer from 4 mb downto 8 bytes.
Copying with test mode without writing to destination file... |
|
 | Byte Manager hexa-edits, merge, concat, extract bytes from, and performs CRC on, any file without size .. |
|
 | Q: I have 3D GameStudio; what do I win with CR Pack and CRED tool?
A: Smaller size of published game. For example, Demo #3 in this package has 7 620 886 bytes uncompressed and 4 200 152 bytes compressed. We have ~55% compression ratio, not so bad.
A: Protection of your work. Password encoding, data compression and encryption used. CR Pack doesn't decompress resources to a hard drive (except you really need it), but into engine's buffers in memory directly. If you use this package, there is no simple solution to steal your work. It is possible, but harder.
A: Full control over resource packages in a source code and good tool CRED (Custom Resources Editor) to manage them.
A: New way to use custom resources: easy replaceable artwork packages, Hidden gifts for customers, etc... |
|
Results in Tags For bytes out
 | TCP Spy .NET is a small application used to trace TCP packets between a client and a server. Optimized for .NET Web Services or Web Site TCP Spy .NET will help you find any bottleneck and it will help you in analyzing your bandwidth usage. With TCP Spy .NET, you can inspect data in different views, track server calls or just redirect the host.
It's a 4 in 1 tool:
- monitoring tool
- web service / web site profiling tool
- redirection server
- Network / Web Site / Web Services spy
Features:
1. General
- Light (one file only)
- Small (less than 1 meg)
- Rich and easy user interface
- Auto update
- Free
2. Monitoring
- Monitor connection IP address
- Monitor connection destination
- Monitor opened connection
- Log connections and requests to file
- Suspend monitoring with no service interruption
- Flag connection / request for an easier tracking
- Insert grid marker for an easier tracking
- View and clear log file
3. Profiling
- Profile Web Service: calls, durations, bytes in, bytes out
- Profile Url: content, size
- Get stats about Web Service (calls, duration, bytes in, bytes out)
- Get stats about Url (calls, duration, bytes in, bytes out)
- Pause profiling without interrupting the communication
- Get the size and the duration of the each request
- View request details for each connections
4. Redirection server
- Configure port redirection
- Configure ip redirection
5. Network spy
- Inspect bytes in data
- Inspect bytes out data
- Inspect header and raw data
- View HTTP header
6. Profesional features
- Hex Data view
- Decompressed Data view with supoprt of gzip and deflate
- Xml Data view
- Image Data View
- Summary view
- Statistic view with chart grouped by Web Service, by content or by url
- Trigger notification unexpected data size or duration
- Run in the tray icon
- Tray icon balloon trigger notification
- Save and load p.. |
|
 | A new protection for programms. Implementing TrialL0CK in programs is very easy and it works with every programming language capable of loading libraries ..
|
|
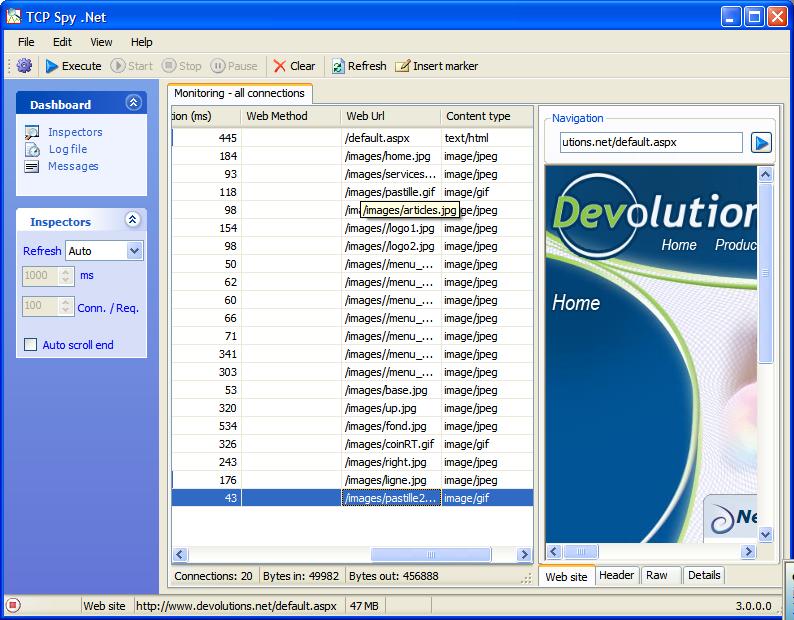 | TCP Spy .NET is a small application used to trace TCP packets between a client and a server. Optimized for .NET Web Services or Web Site TCP Spy .NET will help you find any bottleneck and it will help you in analyzing your bandwidth usage... |
|
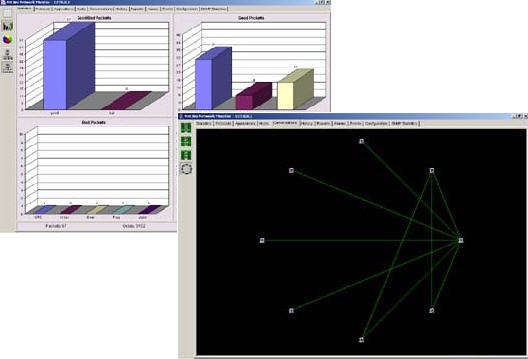 | The Application enables you to see the standard RMON statistics for your whole network segment.
PROTOCOLS
APPLICATIONS
HOSTS
CONVERSATIONS
HISTORY
REPORTS
ALARMS
EVENTS
Real Time
Client-Server..
|
|
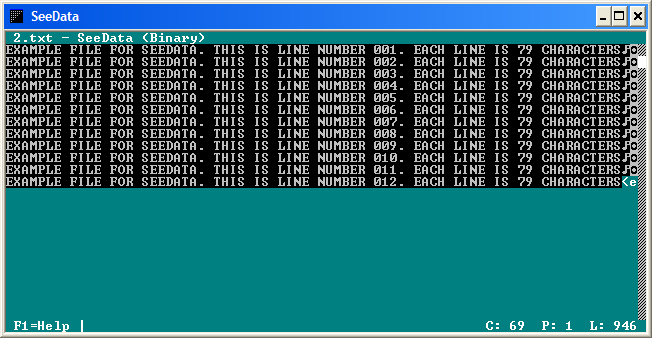 | SeeData is a small console utility that can be used to display the data of any disk file. The file data can currently be displayed in two different formats: Binary or Hex Codes... |
|
 | Feathers :
These are overall features of XP Lan Pro 3.3 (Beta).
XP Lan Pro 3.3 (Beta) can determine following things.
IP address of your computer,
MAC address of LAN card,
Host Name Determination,
Subnet Mask of your network,
DNS Server,
DHCP Server,
Incomming Bytes Per Second,
Outgoing Bytes Per Second,
Incomming Bytes per second Graph,
Outgoing Bytes per second Graph.
In this version XP Lan Pro you can Use System Tray Icon or Bar.You can Change Tray Icon
Lights Colours.When you move you mouse to the tray icon of XP Lan Pro it shows you Total
bytes sent and Total bytes recive...
|
|
 | TEXTCODE, this is an application that takes a binary file and converts it to printable text.This application is similar to endecrypt but it has an output of Printable text. This would allow any type of file, i.e. software, image or text file to be sent as a paper printout by s-mail or messenger. The cipher must be sent separately. It uses an encryption method that is difficult to crack without sophisticated decryption applications. A password generating program will need to have the exact password before any sense can be made of the code.The Textcode application can generate one of two types of file BINHEX (1 binary byte to 2 Text bytes), or an output file that inputs 3 binary bytes and outputs 4 text bytes. In the BINHEX option there is optional encryption using the same engine as endecrypt. It will also take the output file and reconvert it to a binary file. .. |
|
 | Watch your clock - this game is fascinating! Bubblet is an easy but fascinating Logic-Game. Match as much Bubbles in one color in order to burst them! The more are alligned together, the more points you .. |
|
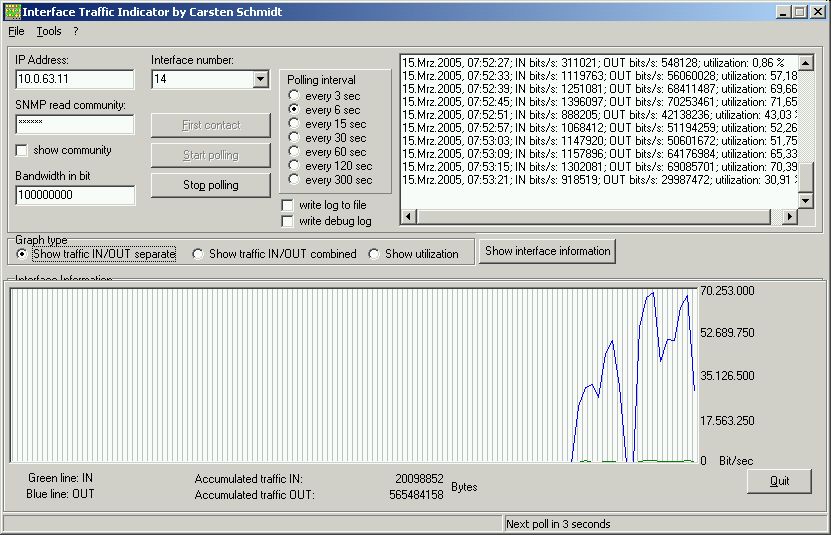 | Interface Traffic Indicator, a graph utility to measure incoming and outgoing traffic on an interface in bits/sec, bytes/sec or utilization. Works on all SNMP-capable interfaces (computers, NICs, switches, routers, etc) with adjustable poll interval... |
|
 | Cyber bandwidth monitor helps keeping a close eye on the comings and goings of your bits and bytes. A graphing tool that shows your PC's upload and download activities in real time. Additionally Cyber Bandwidth Monitor bundles in some useful networking tools, like ping, traceroute, and IMAP and POP email notifiers. The graphs are highly configurable, show upload and/or download traffic, and can monitor any and all network interfaces.
Key Features:
- Graph of bandwidth usage, show download only, upload only, or both.
- Iconified Graph of bandwidth usage in Systray allows hiding of main graph when it is an obstruction.
- Display units in bits or bytes or both.
- Configurable connection speed (graph scale) and update interval.
- Monitor any or all network interfaces installed in your computer.
- Select colors and transparency of the graph.
- Log total bytes, time, and averages to an html or text file.
- View graph of last 24 hours stats.
- URL grabber watches clipboard for URLs, removes line breaks and opens them in your browser.
- Email notifier can check up to 5 POP/IMAP email accounts for new messages periodically.
- Graphic Ping and Traceroute utilities to help diagnose network problems.
- UPnP NAT utility for those who have compatible Internet Gateway Device detected in Windows Networking... |
|
Related search : software software downloadbytes software softwaremodern bytes softwaretcp spyspy netbytes outweb siteweb service,calls duration bytesweb service callsnet standard editionoctet ratepacket ratebytes packetgenerate mostchart showsoctet distribution,byteOrder by Related
- New Release
- Rate
bytes to mb -
bytes converter -
scrapbook bytes -
a.f.9 replace some bytes -
bytes to megabytes -
|
|














